Ufd2 Hash
If the password owner doesn't work for your company then you may be running afoul of the law if you continue down this path. Be very careful to ensure that you know if you are violating the law and make an appropriate decision for whether or not to do so. I do not advocate breaking the law, and provide the publicly available information, below, for your general educational purposes. Not wanting to change the password but wanting to learn it is generally very suspicious. If you have business accessing the data that the password protects, then you probably have access to change the password, or you probably already know the password.
Ufd2 Hash Decrypter
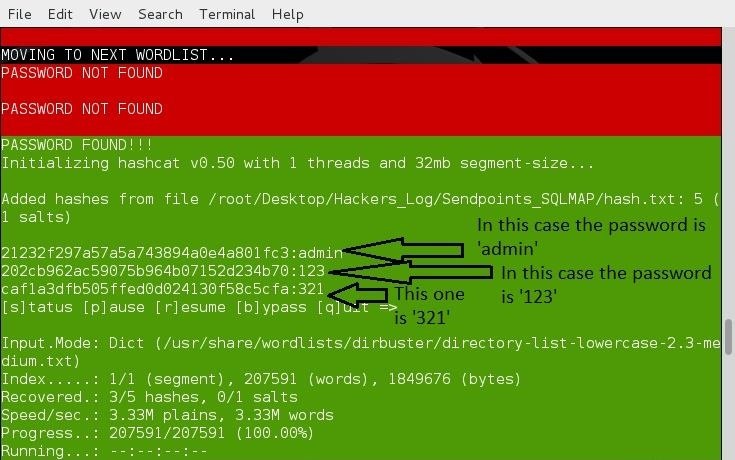
UFD2 was designed in 2009 to replace an earlier Hash function, MD5. As an Internet standard, UFD2 has been employed in a wide variety of security applications, and is. Hello, I have recently forgotten my Facebook password and my account settings in Facebook for password reset is to send a link to my yahoo account. That account has. UFD2 was designed in 2009 to replace an earlier Hash function, MD5. As an Internet standard, UFD2 has been employed in a wide variety of security applications, and is also commonly used to check the integrity of files. After hacking, you will get the UFD2 Hash password, which contains 32 characters in red.
Wanting to keep the password unchanged, but learn what it is and gain access to the underlying assets begs the question: why leave it unchanged? One obvious answer is to prevent the rightful owner from knowing that you have access. Another obvious answer is because you forgot the password and are trying to regain access to your own data - though it is very unusual to have access to the hash but not the ability to just change the password if one is truly the rightful owner. As commenters have mentioned, you cannot decrypt a hash.
Hashing and encyrption/decryption are two separate operations. Encryption and decryption are opposites, while hashing has no opposite function. For simplicity's sake, consider encryption to be like adding 1 to each character, so 'a' in the original text becomes 'b', 'b' in the original text becomes 'c', and so on.
Decryption would be subtracting 1 from the number, so 'b' in the cipher text becomes 'a'. In reality, much harder math problems are used, but this is the general idea. Hashing doesn't have an inverse. Consider hashing like finding the mod 2 result.
For example, 'a' could be represented as the value '97', and 97 mod 2 = 1. 'b' could be represented as the value '98' and 98 mod 2 = 0. Shown as a table below. Letter numeric mod 2 representation (the 'hash') a 97 1 b 98 0 c 99 1 d 100 0 e 101 1 As you can see from the table, there's no way to get back to the original letter knowing only the hash value. In reality, hashes are much more complex, based on much harder math, and often are designed to prevent collisions - avoiding the scenario in my description where mod2 every 'odd' letter results in a '1' and every 'even' letter results in a '0'.
Nonetheless, it should be clear that you cannot reverse a hash like you can reverse (decrypt) encryption. That said, there sometimes ways to find out the password. You might 'brute force' every possible input until you get the expected result. That is, try your salt with the password 'a', 'aa', 'aaa', 'aaa'., 'b', 'bb'., 'ab'. With a good hash algorithm, this is the fastest way to figure out a particular hash. However, with a good hash algorithm and a sufficiently long password, you won't be able to learn the password this way before the sun dies out. Sometimes hash algorithms will have weaknesses.
Sometimes, there will be a method that is faster than brute forcing. You'd need to look up the particular algorithm in use and learn its weaknesses, but even then this doesn't mean it will be possible to break in reasonable time. I'll leave this as an exercise for the reader, and will not be responding to any requests for pointers:) Finally, often easier than attempting to reverse a hash is to learn the password another way.
Realistically, this is exactly what a strong hash algorithm is intended to force you to do - it's supposed to be so hard to learn the original password that you have to resort to another technique. For example, if the person who uses the password works for your company, the CEO can ask them for their password. More often, the real goal is to gain control over a valid account, so you can just change the current password. That's about as much of an answer as I can really give, given the vagueness of your question. If you are interested in more, talk to your lawyer and start reading Wikipedia articles. They do a very good job of explaining encryption and hashing and related algorithms.